Access and Security#
API tokens (keys) authorize access to IEX Cloud Data. Tokens allow you to track, control, and throttle data usage. You can grant people access to data by giving them publishable tokens.
Note
We provide a valid, signed certificate for our endpoints. Make sure your connection library supports HTTPS with the SNI extension.
API Tokens#
IEX Cloud provides two types of API tokens: publishable and secret.
Publishable API tokens are meant solely to identify your account; they aren’t secret. They can be published in places like your website code or mobile app code.
Secret API tokens should be kept confidential and should only be stored on your own secure servers. Your account’s secret API token can perform any API request authorized for your account.
Warning
Your secret token (aka secret key) allows you to perform any action on behalf of your account. NEVER share your secret token publicly.
Token Protection Tips#
Keep your secret token safe. Your secret token can make any API call on behalf of your account, including changes that may impact billing. Never store your secret token in a source control system. Never use your secret token outside your web server in places such as a browser, mobile app, or distributed file.
Monitor account usage for anomalies. If you observe unauthorized or abnormal usage, regenerate or remove your API token in the Console.
Do not embed API tokens directly in code. Instead of directly embedding API tokens in your application’s code, put them in environment variables or include them in files that are stored separately from the bulk of your code–store them outside your application’s source code repository. Then, if you share your code, the API tokens are not included in the shared files.
Do not store API tokens in inside your application’s source control. If you store API tokens in files, keep the files outside your application’s source control system. This is particularly important if you use a public source code management system repository such as a public GitHub repo.
Limit access with restricted tokens. In the Console’s API Tokens page, you can associate IP addresses or referrer URLs with each token, reducing the impact of a compromised API token.
Use independent API tokens for different apps. This limits each token’s access scope. If an API token is compromised, you can replace the impacted token without impacting other API tokens.
Note
Regenerating or removing a token disables its access to the API within 10 seconds.
Creating an API Token#
Here’s how to create and use a publishable API token.
Go to API Tokens. It’s listed in your user menu.
The API Tokens page appears, listing your tokens in order, oldest to newest.
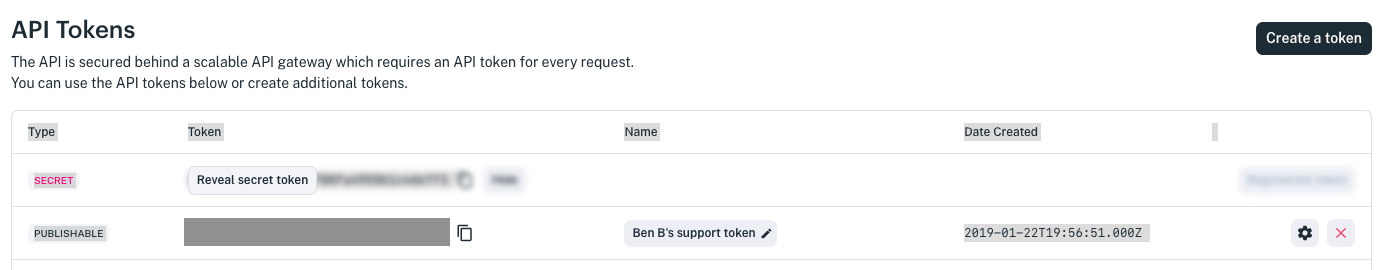
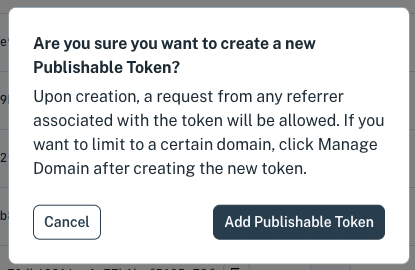
Click Create a token. A dialog window appears and asks if you are sure you want to add a publishable token.
Note
Publishable tokens have IEX Cloud Data (Core Data) read access by default.
Click Add publishable token. A new publishable token is added to the bottom of the token list.
Edit the token by finding it at the bottom of the token list and clicking on its gear icon or on its token ID. The API token form appears.
Define the token.
Nickname: Enter a meaningful name.
Signed Requests: Enables requiring a signature per request.
Core Data Access: Read access to IEX Cloud Data is granted by default. You can alternatively revoke this access.
Premium Data Access: Grants access to Premium Data (requires Premium Data subscription)
Dataset permissions: Grants read/write/delete access to specified datasets.
DEPRECATED
Apperate and its features (including this feature) are deprecated and planned for removal.
Allowed Domain(s): Leaving blank allows requests with the token from any domain. Specifying a domain(s) limits requests to be from that domain(s). Read more at Restrict Data Access to Specific Domains.
Core Credit Usage Limit: Restricts the number of core credits available to the token.
The token below, for example, can access Core Data and Premium Data, and has read access to three datasets.
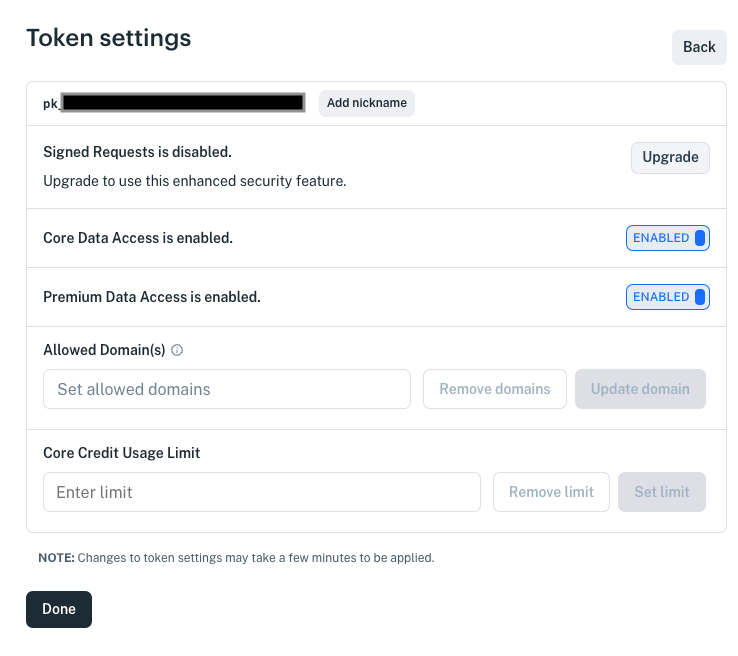
When you’re done specifying the token, click Done. The token’s permissions take affect in a couple minutes. Then you can make the specified API calls using the token.
Note
A token’s permissions take affect a couple minutes after creating the token.
Now the token can be used in calling the specified APIs.
How many tokens do I need?#
The number of tokens you may need depends on the number of customers and team members that you want to grant access to, the datasets they need, and in the case of team members, the actions they need to perform on your Apperate resources and your datasets. You’ll typically want to use multiple tokens when tracking, controlling, and throttling usage for different projects, apps, or end users separately.
What’s Next?#
Ready to call some data APIs? See Query Data.
Want to get your teammates involved? Learn how to add teammates at Manage Users.